Challenges
The Strangler Fig pattern requires weighing the initial investment against the long-term benefits and is not without its challenges.
Each application brings its unique set of obstacles, and navigating these is a critical part of the process.
Some challenges when implementing this pattern include:
Infrastructure
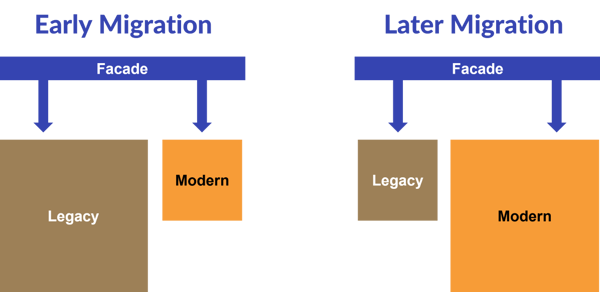
A significant consideration when implementing the Strangler Fig pattern is the heightened infrastructure complexity it introduces. Instead of managing a single application, you now have two separate applications to oversee, along with the proxy layer.
It's essential to ensure that your team is equipped with the necessary skills to handle this complexity. This situation often calls for robust DevOps expertise, in addition to the regular development skills.
In this context, having solid Continuous Integration/Continuous Deployment (CI/CD) pipelines is more than just beneficial – it's a necessity.
Additionally, ensure a well-thought-out branching strategy is used, especially if Business As Usual (BAU) and maintenance activities are being carried out alongside the migration.
Two Backoffices
A prominent hurdle is the potential of ending up with two separate CMS back offices.
This issue could be a sticking point for some clients. However, if they're open to the process, there are strategies we can implement to alleviate the burden.
When segmenting the application, aim to focus on specific content areas that fall under a single core tree node at a time. This approach can make the transition more manageable.
Additionally, integrating helpful messaging and direct links to the new CMS within the old back office can be incredibly useful.
Other Key Technical Considerations
Other considerations will vary based on the specifics of your project and may include:
- Migrating content & media
- Site search
- Sharing session state
- User authentication & identity
- Application linking connectivity & fault tolerance
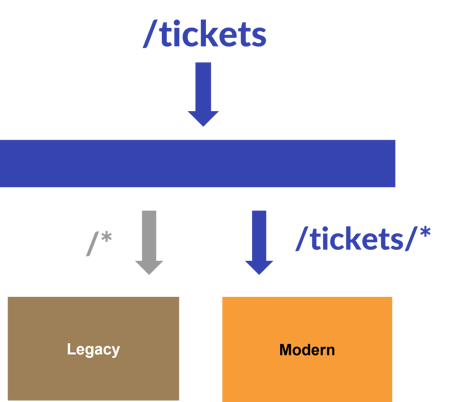
- Redirects, HTTP headers, server variables